Configure Connection to Data Source¶
Alation Cloud Service Applies to Alation Cloud Service instances of Alation
Customer Managed Applies to customer-managed instances of Alation
After you install the Oracle OCF connector, you must configure the connection to the Oracle data source.
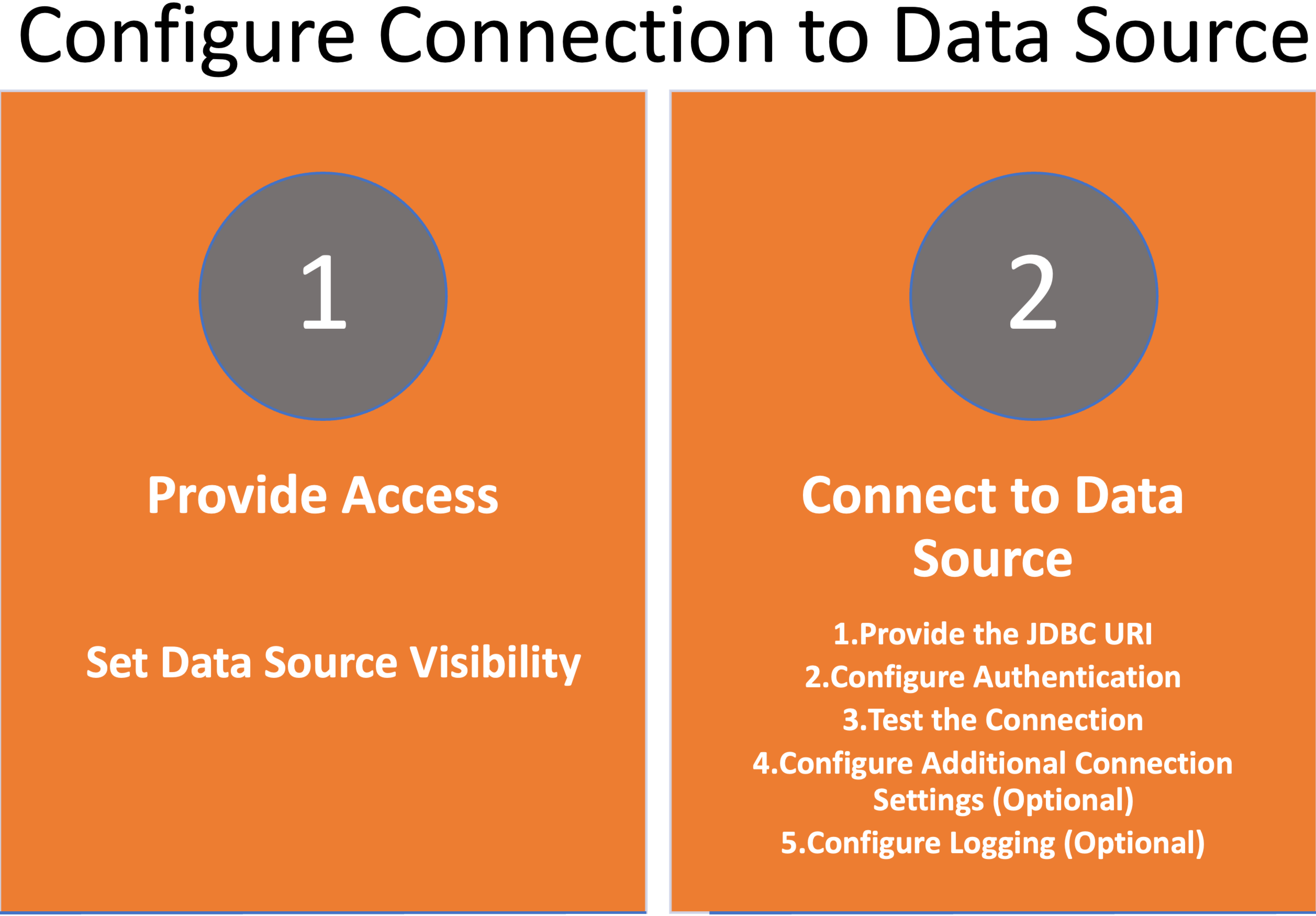
The various steps involved in configuring the Oracle data source connection setting are:
Provide Access¶
Go to the Access tab on the Settings page of your Oracle data source, set the data source visibility using these options:
Public Data Source — The data source is visible to all users of the catalog.
Private Data Source — The data source is visible to the users allowed access to the data source by Data Source Admins.
You can add new Data Source Admin users in the Data Source Admins section.
Connect to Data Source¶
To connect to the data source, you must perform these steps:
Important
The Alation user interface displays standard configuration settings for credentials and connection information stored in the Alation database. If your organization has configured Azure KeyVault or AWS Secrets Manager to hold such information, the user interface will change to include the following buttons adjacent to the respective fields:
By default, you see the user interface for Standard. In the case of Vault, instead of the actual credential information, you must select the source and provide the corresponding key. For details, see Configure Secrets for OCF Connector Settings.
Provide the JDBC URI¶
JDBC URI¶
When building the URI, include the following information:
Hostname or IP of the instance
Port number
Service name
Service account username
Password
URI Format¶
oracle:thin:@//<Hostname_or_IP>:<Port_Number>/<Service_Name>
Example
oracle:thin:@//ifac-orcl.ceeyrlqdpprr.us-west-2.rds.amazonaws.com:1521/orcl
Use this JDBC URI format for Basic and Kerberos authentication without SSL connection.
JDBC URI for SSL Authentication¶
For SSL authentication, use the TCPS protocol and the following JDBC URI format:
oracle:thin:@(DESCRIPTION=(ADDRESS=(PROTOCOL=TCPS)(HOST=<Hostname_or_IP>)(PORT=<Port_Number>))(CONNECT_DATA=(SID=<Service_Name>)))
Use this format to enable SSL authentication.
JDBC URI for LDAP Authentication¶
URI Format¶
oracle:thin:@ldap://<Hostname or IP >:<Port>/<servicename>,<LDAP Context>
Example
oracle:thin:@ldap://ip-10-13-52-95.test.com:389/alation,cn=OracleContext,dc=alation-test,dc=com
Connect Using Native Network Encryption (NNE)¶
NNE encrypts database connections without the need to configure TCP/IP and SSL/TLS and to open and listen on different ports. There are multiple configuration options for NNE. You may come across different scenarios where you need to pass different parameters in the JDBC URI to connect, depending on how NNE was configured on your Oracle database. For more information, refer to the Oracle official documentation on NNE.
Consider the following scenarios for NNE:
Scenario 1 (Default):¶
No settings done on the Oracle server.
Pass extra parameters in JDBC URI as shown below:
oracle:thin:@//<Hostname_or_IP>:<Port_Number>/<Service_Name>? oracle.net.encryption_client=REQUIRED &oracle.net.encryption_types_client=AES256 &oracle.net.crypto_checksum_client=REQUIRED &oracle.net.crypto_checksum_types_client=SHA256
This will allow Oracle to enable the NNE encryption.
Scenario 2:¶
This scenario applies if you are using one algorithm for encryptions and another for checksum.
This corresponds to the following configuration in the sqlnet.ora file on the Oracle server:
SQLNET.ENCRYPTION_SERVER = ACCEPTED SQLNET.CRYPTO_CHECKSUM_SERVER = ACCEPTED SQLNET.CRYPTO_CHECKSUM_TYPES_SERVER= (SHA256) SQLNET.ENCRYPTION_TYPES_SERVER= (AES256)In the above configuration, AES256 is used for encryption and SHA256 is used for checksum.
If this is your case, you need to add the following parameters to the JDBC URI you provide in Alation:
oracle:thin:@//10.13.80.110:1521/alation? oracle.net.encryption_client=REQUIRED &oracle.net.encryption_types_client=<Encryption mechanism allowed on Oracle server> &oracle.net.crypto_checksum_client=REQUIRED &oracle.net.crypto_checksum_types_client=<Checksum mechanism allowed on Oracle server>
Provide the JDBC URI in Alation¶
To provide to the JDBC URI in the Alation UI, perform these steps:
From Alation version 2023.3.4 and connector version 1.5.0
On the Settings page of your Oracle data source, go to the General Settings tab.
In the Provide the JDBC URI section, based on the type of authentication you want to use, enter the JDBC URI. For details, see Provide the JDBC URI .
Note
Click the View history icon to view the history of recent URI values provided by users, if any. The History: Recent URI Values list displays 100 URI entries. You can copy a URI from the list to reuse.
Click Save.
On the Settings page of your Oracle data source, go to the General Settings tab.
Go to the Connector Settings > Datasource connection section and based on the type of authentication you want to use, enter the JDBC URI. For details, see Provide the JDBC URI .
Click Save.
Configure Authentication¶
Alation supports the following authentication types for the Oracle data source:
Basic authentication (database username and password)
Kerberos authentication
LDAP authentication
SSL authentication
Basic Authentication¶
Basic authentication requires a service account username and password.
Configure Basic Authentication¶
From Alation version 2023.3.4 and connector version 1.5.0
On the Settings page of Oracle data source, go to the General Settings tab.
In the Configure authentication step, click on the Basic tab.
Provide the service account username and password.
To use SSL with Basic authentication, turn on the Enable SSL toggle, provide the Truststore password, and upload the SSL certificate.
Note
To use SSL authentication, ensure that you have provided the JDBC URI format for TCPS protocol. See JDBC URI for SSL Authentication.
The Oracle OCF connector supports .crt file for SSL certificate.
Click Save.
On the Settings page of your Oracle data source, click on the General Settings tab.
Go to the Connector Settings > Datasource connection section and provide the following information:
Parameter
Description
Username
Specify the service account username.
Password
Specify the service account password.
To use SSL with Kerberos, turn on the Enable SSL toggle, provide the Truststore password, and upload the SSL certificate.
Note
To use SSL authentication, ensure that you have provided the JDBC URI format for TCPS protocol. See JDBC URI for SSL Authentication.
The Oracle OCF connector supports .crt file for SSL certificate.
Click Save.
Kerberos Authentication¶
Alation supports Kerberos authentication with password and keytab.
Have the krb5.conf and the keytab files ready for upload when configuring the data source in Alation.
Configure Kerberos Authentication with Password¶
From Alation version 2023.3.4 and connector version 1.5.0
On the Settings page of Oracle data source, go to the General Settings tab.
In the Configure authentication step, click on the Kerberos with password tab.
Provide the service account username, password, and upload the krb5.conf file using the Upload krb5.conf link.
To use SSL with Kerberos, turn on the Enable SSL toggle, provide the Truststore password, and upload the SSL certificate..
Note
To use SSL authentication, ensure that you have provided the JDBC URI format for TCPS protocol. See JDBC URI for SSL Authentication.
The Oracle OCF connector supports .crt file for SSL certificate.
Click Save.
On the Settings page of your Oracle data source, click on the General Settings tab.
Go to the Connector Settings > Datasource connection section and provide the following information:
Parameter
Description
Username
Specify the service account username.
Password
Specify the service account password.
Enable Kerberos authentication
Select this checkbox and upload the krb5.conf file using the upload link under the checkbox.
To use SSL with Kerberos, turn on the Enable SSL toggle, upload the SSL certificate, and provide the Truststore password.
Note
To use SSL authentication, ensure that you have provided the JDBC URI format for TCPS protocol. See JDBC URI for SSL Authentication.
The Oracle OCF connector supports .crt file for SSL certificate.
Click Save.
Configure Kerberos Authentication with Keytab¶
From Alation version 2023.3.4 and connector version 1.5.0
On the Settings page of Oracle data source, go to the General Settings tab.
In the Configure authentication step, click on the Kerberos with keytab tab.
Provide the service account username and upload the krb5.conf file using the Upload krb5.conf link.
To use SSL with Kerberos, turn on the Enable SSL toggle, provide the Truststore password, and upload the SSL certificate.
Note
To use SSL authentication, ensure that you have provided the JDBC URI format for TCPS protocol. See JDBC URI for SSL Authentication.
The Oracle OCF connector supports .crt file for SSL certificate.
Click Save.
On the Settings page of your Oracle data source, click on the General Settings tab.
Go to the Connector Settings > Datasource connection section and provide the following information:
Parameter
Description
Username
Specify the service account username.
Password
Not applicable
Use keytab
Select this checkbox if using keytab and upload the keytab file for the service account using the upload link under the checkbox.
To use SSL with Kerberos, turn on the Enable SSL toggle and upload the SSL certificate.
Note
To use SSL authentication, ensure that you have provided the JDBC URI format for TCPS protocol. See JDBC URI for SSL Authentication.
The Oracle OCF connector supports .crt file for SSL certificate.
Click Save.
LDAP Authentication¶
If you are using LDAP authentication, check the following settings on your Oracle LDAP server:
Check that the file
$ORACLE_HOME/network/admin/ldap.oraexists on the LDAP server. See an example below:# ldap.ora # Place this file in the network/admin subdirectory of your # $ORACLE_HOME location DIRECTORY_SERVERS = (ip-10-13-52-95.alation-test.com:389:636) DEFAULT_ADMIN_CONTEXT = "dc=alation-test,dc=com" DIRECTORY_SERVER_TYPE = OIDIn this example:
ip-10-13-52-95.alation-test.com:389:636—Hostname(s) and port number(s) of the LDAP directory server(s).
"dc=alation-test,dc=com"—Default directory entry.You should use your specific values instead.
For more details about the ldap.ora file, refer to the Oracle documentation: Directory Usage Parameters in the ldap.ora File.
If you don’t have the ldap.ora file in the directory $ORACLE_HOME/network/admin/, then create it and add the content based on the example above. Use your specific property values in the file.
Configure LDAP Authentication¶
From Alation version 2023.3.4 and connector version 1.5.0
On the Settings page of Oracle data source, go to the General Settings tab.
In the Configure authentication step, click on the Basic tab.
Note
Ensure that you have provided the JDBC URI format applicable for LDAP authentication. See JDBC URI for SSL Authentication.
Provide the service account username and password.
To use SSL with LDAP, turn on the Enable SSL toggle, provide the Truststore password, and upload the SSL certificate.
Note
To use SSL authentication, ensure that you have provided the JDBC URI format for TCPS protocol. See JDBC URI for SSL Authentication.
The Oracle OCF connector supports .crt file for SSL certificate.
Click Save.
On the Settings page of your Oracle data source, click on the General Settings tab.
Go to the Connector Settings > Datasource connection section and provide the following information:
Note
Ensure that you have provided the JDBC URI format applicable for LDAP authentication. See JDBC URI for SSL Authentication.
Parameter
Description
Username
Specify the service account username.
Password
Specify the service account password.
To use SSL with Kerberos, turn on the Enable SSL toggle, provide the Truststore password, and upload the SSL certificate.
Note
To use SSL authentication, ensure that you have provided the JDBC URI format for TCPS protocol. See JDBC URI for SSL Authentication.
The Oracle OCF connector supports .crt file for SSL certificate.
Click Save.
Testing LDAP Connection¶
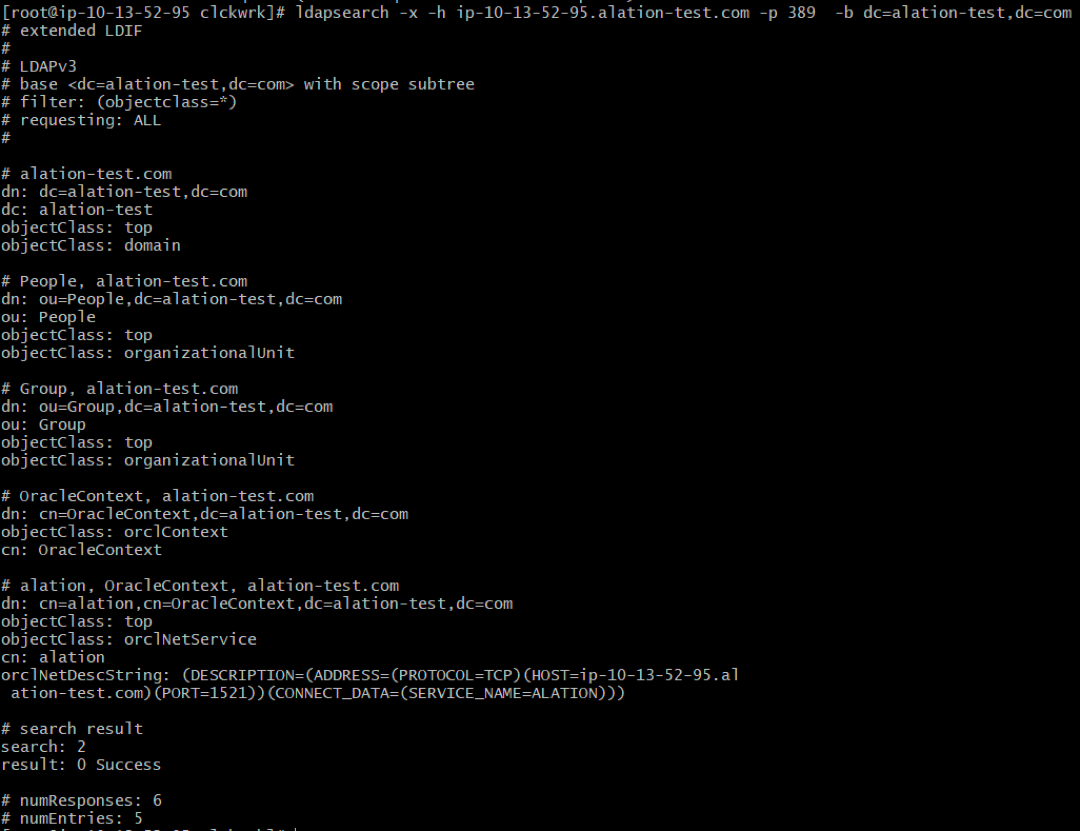
You can test the connection over LDAP to your Oracle database from the Alation host using an ldapsearch tool, for example:
ldapsearch -x -h ip-10-13-52-95.alation-test.com -p 389 -b dc=alation-test,dc=com
You should receive a control response similar to the following:
Test the Connection¶
The connection test checks database connectivity. Alation uses the JDBC URI to connect to the database and to confirm when the connection is established.
After specifying the JDBC URI and configuring authentication, test the connection.
To validate the network connectivity, go to General Settings > Test Connection on the Settings page of your Oracle data source and click Test.
A dialog box appears confirming the status of the connection test.
Configure Additional Connection Settings¶
Apart from the mandatory configurations that you perform to connect to the data source in the General Settings tab, you can configure the following additional settings:
Configure Additional Data Source Connections
Disable Obfuscate Literals
Disable automatic lineage generation
Configure Additional Data Source Connections¶
Alation can associate objects in a data source with objects in another source in the catalog through lineage. For example, you can show lineage between your data source and BI sources that use its data.
Provide additional connection information for the data source to see lineage across multiple sources on the Lineage chart.
From Alation version 2023.3.4 and connector version 1.5.0.
To enter additional data source connection details, go to General Settings > Advanced settings of the Settings page of your Oracle connector and enter the connection URL.
Use the following format:
<host>:<port>You can provide multiple values as a comma-separated list:
<host1>:<port1>,<host2>:<port2>For example:
10.13.71.216:1541,sever.com:1542
On the Application Settings section of General Settings tab, provide the host and port information in the Additional data source connections field.
This parameter is used to generate lineage between the current data source and another source in the catalog, for example a BI source that retrieves data from the underlying database. The parameter accepts host and port information of the corresponding BI data source connection.
Use the following format: <host>:<port>
You can provide multiple values as a comma-separated list:
<host1>:<port1>,<host2>:<port2>
For example:
10.13.71.216:1541,sever.com:1542
For more details, see Configure Cross-Source Lineage.
Enable or Disable Obfuscate Literals¶
You can hide literal values from queries ingested with query log ingestion and displayed on the Queries tab of a schema and table catalog objects.
From Alation version 2023.3.4 and connector version 1.5.0.
Go to the General Settings tab and turn on or off the Obfuscate literals toggle under the Advanced settings section.
Go to the General Settings tab and turn on or off the Obfuscate literals toggle.
When enabled, literal values are substituted with placeholder values. Disable this option when you want literal values in queries to be visible to users.
By default, this option is disabled.
Configure Logging¶
To set the logging level for your Oracle data source logs, perform these steps:
From Alation version 2023.3.4 and connector version 1.5.0.
On the Settings page of your Oracle data source, go to General Settings > Connector logs.
Select a logging level for the connector logs and click Save.
The available log levels are based on the Log4j framework.
On the Settings page of your Oracle data source, go to Logging configuration section of General Settings tab.
Select a logging level for the connector logs and click Save.
The available log levels are based on the Log4j framework.
You can view the connector logs in Admin Settings > Server Admin > Manage Connectors > Oracle OCF connector.